- All
- Product Name
- Product Keyword
- Product Model
- Product Summary
- Product Description
- Multi Field Search
| Availability: | |
|---|---|

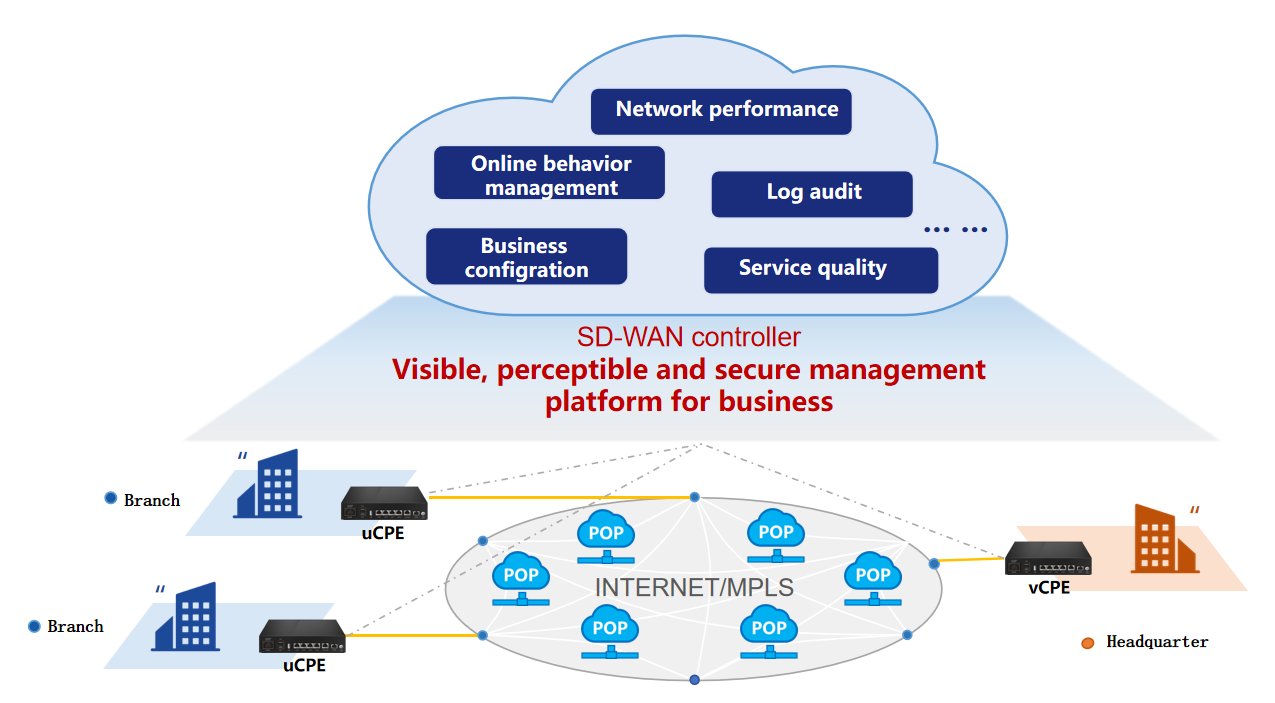
SD-WAN devices offer a service that applies SDN technology to wide area network interconnection scenarios. The SD-WAN overlay network technology can mask the complexity of the physical network and integrates various technologies from terminals, pipelines, and the cloud, forming a technological innovation. Its main features include: user on-demand, zero-touch configuration, cloud and application awareness, wide area acceleration, flexible billing, etc.
The SD-WAN product is a highly reliable and flexible intelligent access gateway designed for enterprise users. The product supports wired, 4G, and 5G access methods, meeting the needs of operators or enterprises to provide broadband, data transmission, video conferencing, and other functions to users through IP access methods. At the same time, it can be centrally managed through a centralized policy management platform, realizing services such as device initialization registration authentication, service orchestration, tenant management, and operation and maintenance management.
Depending on the application scenario, the devices can be divided into uCPE (terminal device), vCPE (central office device), and the centralized policy management platform (controller).
SD-WAN devices offer a service that applies SDN technology to wide area network interconnection scenarios. The SD-WAN overlay network technology can mask the complexity of the physical network and integrates various technologies from terminals, pipelines, and the cloud, forming a technological innovation. Its main features include: user on-demand, zero-touch configuration, cloud and application awareness, wide area acceleration, flexible billing, etc.
The SD-WAN product is a highly reliable and flexible intelligent access gateway designed for enterprise users. The product supports wired, 4G, and 5G access methods, meeting the needs of operators or enterprises to provide broadband, data transmission, video conferencing, and other functions to users through IP access methods. At the same time, it can be centrally managed through a centralized policy management platform, realizing services such as device initialization registration authentication, service orchestration, tenant management, and operation and maintenance management.
Depending on the application scenario, the devices can be divided into uCPE (terminal device), vCPE (central office device), and the centralized policy management platform (controller).





Diverse interfaces, load balancing: SD-WAN no longer enforces the exclusive use of MPLS, but allows for multiple connection types including MPLS, the Internet, Ethernet, 4G LTE, and 5G APN. It supports the rapid provisioning of dedicated line services without the need to specify a service provider, enabling cross-operator provisioning.
Self-selecting the optimal path: SD-WAN's uCPE and vCPE can autonomously choose the best path based on the current network conditions and configuration policies.
Simple deployment, completed in seconds: Zero-contact deployment of devices, meaning plug-and-play. Through the centralized policy management platform, uCPE can automatically obtain configurations after being powered on.
VPN encryption, transmission security assurance: By using Ipsec or TLS/DTLS encryption to protect data in transit, integrating NFV technology; conveniently introducing NGFW firewall technology, Intrusion Prevention Systems (IPS), cloud security services.
Intelligent routing, ensuring critical applications: Intelligent routing technology can enhance the reliability of Wide Area Network (WAN) connections and improve transmission efficiency. Real-time link quality monitoring, comprehensively and in real-time, assesses the quality of each link - packet loss/delay/jitter.
End-to-end QoS Management: Ensuring high-priority applications, accelerating application access speed through wide area network acceleration technologies, and improving user experience.
Link Smooth Switching: Smoothly switch traffic to other available links when a link is unavailable, with failover occurring within 2-3 packet drops, and the lost packets can be retransmitted and reordered.
Diverse interfaces, load balancing: SD-WAN no longer enforces the exclusive use of MPLS, but allows for multiple connection types including MPLS, the Internet, Ethernet, 4G LTE, and 5G APN. It supports the rapid provisioning of dedicated line services without the need to specify a service provider, enabling cross-operator provisioning.
Self-selecting the optimal path: SD-WAN's uCPE and vCPE can autonomously choose the best path based on the current network conditions and configuration policies.
Simple deployment, completed in seconds: Zero-contact deployment of devices, meaning plug-and-play. Through the centralized policy management platform, uCPE can automatically obtain configurations after being powered on.
VPN encryption, transmission security assurance: By using Ipsec or TLS/DTLS encryption to protect data in transit, integrating NFV technology; conveniently introducing NGFW firewall technology, Intrusion Prevention Systems (IPS), cloud security services.
Intelligent routing, ensuring critical applications: Intelligent routing technology can enhance the reliability of Wide Area Network (WAN) connections and improve transmission efficiency. Real-time link quality monitoring, comprehensively and in real-time, assesses the quality of each link - packet loss/delay/jitter.
End-to-end QoS Management: Ensuring high-priority applications, accelerating application access speed through wide area network acceleration technologies, and improving user experience.
Link Smooth Switching: Smoothly switch traffic to other available links when a link is unavailable, with failover occurring within 2-3 packet drops, and the lost packets can be retransmitted and reordered.
Hardware Specifications-1 | ||||
Product Model | SEG-100AV16L | SEG-100A V26L | ||
Dimensions (D*W*H) | 1U 330*435*44mm | 1U 450*435*44.5mm | ||
Memory | 4G | 8G | ||
USB Interface | 2 | 2 | ||
Gigabit Electrical Port/Optical Port | 8GE+4SFP | 6GE+2SFP | ||
Number Of Expansion Slots | 1 | 2 | ||
Control Interface | 1 (local) | |||
4G/5G | Not supported | |||
WIFI | Not supported | |||
Shell | Metal material | |||
| Hardware Specifications-2 | ||||
Product Model | SEG-100A V30L | SEG-100A V60L | SEG-100AV80L/V80H | |
Dimensions (D*W*H) | 2U 500*435*88mm | 2U 500*435*88mm | 2U 600*440*88mm | |
Memory | 8G | 16G | 32G | |
USB Interface | 2 | 2 | 2 | |
Gigabit Electrical Port/Optical Port | 6GE+4SFP | 6GE+4SFP | 无 | |
Number Of Expansion Slots | 2 | 6 | 8 | |
Control Interface | 1 (local) | |||
4G/5G | Not supported | |||
WIFI | Not supported | |||
Shell | Metal material | |||
| Software Specifications | ||||
Safety Protection | Firewall Access Control: Supports policy pre-compilation to ensure that firewall performance does not degrade in the case of a large number of complex policies. | |||
Session Control: Connection count and connection rate control policies based on interface/security domain, address, user, service, application, and time parameters. | ||||
Intrusion Prevention: Intrusion prevention features in IPV4/IPV6 environments; supports setting of intrusion prevention policies. | ||||
Antivirus: Supports virus scanning for files under HTTP, FTP, POP3, IMAP, SMTP protocols, supports setting of antivirus policies. | ||||
Web Application Protection: Implementing application layer security protection for Web services based on SQL injection and XSS attack algorithms | ||||
Anti-Denial of Service Attack: Supports TCP Flood protection, UDP Flood protection, ICMP Flood protection, and DoS protection; | ||||
ARP Attack Protection: Supports IP-MAC binding, uniqueness checking, and active protection, supports anti-ARP spoofing and ARP Flood attack prevention. | ||||
Blacklist: Supports IP-based blacklist functionality | ||||
Application Behavior Management And Control | Intelligent Recognition Application: Accurately recognize mainstream applications | |||
Application Control: Based on intelligent application identification, it provides application behavior control features. | ||||
Software Control: Supports the identification of software and the management of individual software (social media software), and supports black and white list management based on QQ/WeChat IDs. | ||||
URL Category Filtering: Supports classified management and control of website access. | ||||
Support for search engine application control, P2P download application control, video application control, and email application control. | ||||
Support application feature library, application classification, and application feature library upgrade. | ||||
Traffic Control And Quality Of Service (QoS) | Line settings: Supports line bandwidth settings based on physical interfaces or VLAN interfaces. | |||
Application-based flow control pipeline: Supports the definition of flow control pipelines based on source IP address, destination IP address, application, service port, and time. | ||||
Supports multi-layer pipeline nesting, bandwidth control, bandwidth assurance, setting pipeline priorities, automatic traffic shaping | ||||
Network | Supports the simultaneous operation of IPV6/IPV4 dual-stack, all security features are supported for use under the dual-stack. | |||
Supports VLAN, transparent bridge interface, interface linkage, link aggregation | ||||
Supports static routing, equivalent routing, supports static route weights, supports BFD check. | ||||
Dynamic Routing: Supports dynamic routing protocols such as RIPv1, RIPv2, OSPFv2 (with BFD detection), and BGP4. | ||||
Strategy Routing: Supports policy-based routing based on incoming interface, source IP, destination IP, etc. | ||||
Link Load Balancing: Provides various load balancing algorithms, supports dual health checks for links, and supports setting priorities and weights for links. | ||||
Supports health check, session persistence, NAT, ALG, VPN, STP, DNS Server, DNS records, DNS transparent proxy, etc. | ||||
High Availability | Supports dual-active hot backup, standby management, VRRP protocol, HA failover conditions and logic, connection session synchronization, setting preemption priority. | |||
Monitoring | Threat visualization, application traffic visualization, user traffic visualization, interface traffic display, system operation information. | |||
Log Report | Storage and export functions for various local logs, supporting log grading; supports remote Syslog logging and supports multiple Syslog servers. | |||
The system provides traffic reports and threat reports, supports email alerts, and allows for the definition of custom email alerts to be triggered under specific conditions. | ||||
Management And Configuration | Supports centralized management, centralized policy analysis, Web management interface, custom packet capture, network debugging. | |||
Backup and recovery of system configuration, administrator login and permission hierarchy; supports SNMP (V1/V2/V3), NTP time synchronization | ||||
Hardware Specifications-1 | ||||
Product Model | SEG-100AV16L | SEG-100A V26L | ||
Dimensions (D*W*H) | 1U 330*435*44mm | 1U 450*435*44.5mm | ||
Memory | 4G | 8G | ||
USB Interface | 2 | 2 | ||
Gigabit Electrical Port/Optical Port | 8GE+4SFP | 6GE+2SFP | ||
Number Of Expansion Slots | 1 | 2 | ||
Control Interface | 1 (local) | |||
4G/5G | Not supported | |||
WIFI | Not supported | |||
Shell | Metal material | |||
| Hardware Specifications-2 | ||||
Product Model | SEG-100A V30L | SEG-100A V60L | SEG-100AV80L/V80H | |
Dimensions (D*W*H) | 2U 500*435*88mm | 2U 500*435*88mm | 2U 600*440*88mm | |
Memory | 8G | 16G | 32G | |
USB Interface | 2 | 2 | 2 | |
Gigabit Electrical Port/Optical Port | 6GE+4SFP | 6GE+4SFP | 无 | |
Number Of Expansion Slots | 2 | 6 | 8 | |
Control Interface | 1 (local) | |||
4G/5G | Not supported | |||
WIFI | Not supported | |||
Shell | Metal material | |||
| Software Specifications | ||||
Safety Protection | Firewall Access Control: Supports policy pre-compilation to ensure that firewall performance does not degrade in the case of a large number of complex policies. | |||
Session Control: Connection count and connection rate control policies based on interface/security domain, address, user, service, application, and time parameters. | ||||
Intrusion Prevention: Intrusion prevention features in IPV4/IPV6 environments; supports setting of intrusion prevention policies. | ||||
Antivirus: Supports virus scanning for files under HTTP, FTP, POP3, IMAP, SMTP protocols, supports setting of antivirus policies. | ||||
Web Application Protection: Implementing application layer security protection for Web services based on SQL injection and XSS attack algorithms | ||||
Anti-Denial of Service Attack: Supports TCP Flood protection, UDP Flood protection, ICMP Flood protection, and DoS protection; | ||||
ARP Attack Protection: Supports IP-MAC binding, uniqueness checking, and active protection, supports anti-ARP spoofing and ARP Flood attack prevention. | ||||
Blacklist: Supports IP-based blacklist functionality | ||||
Application Behavior Management And Control | Intelligent Recognition Application: Accurately recognize mainstream applications | |||
Application Control: Based on intelligent application identification, it provides application behavior control features. | ||||
Software Control: Supports the identification of software and the management of individual software (social media software), and supports black and white list management based on QQ/WeChat IDs. | ||||
URL Category Filtering: Supports classified management and control of website access. | ||||
Support for search engine application control, P2P download application control, video application control, and email application control. | ||||
Support application feature library, application classification, and application feature library upgrade. | ||||
Traffic Control And Quality Of Service (QoS) | Line settings: Supports line bandwidth settings based on physical interfaces or VLAN interfaces. | |||
Application-based flow control pipeline: Supports the definition of flow control pipelines based on source IP address, destination IP address, application, service port, and time. | ||||
Supports multi-layer pipeline nesting, bandwidth control, bandwidth assurance, setting pipeline priorities, automatic traffic shaping | ||||
Network | Supports the simultaneous operation of IPV6/IPV4 dual-stack, all security features are supported for use under the dual-stack. | |||
Supports VLAN, transparent bridge interface, interface linkage, link aggregation | ||||
Supports static routing, equivalent routing, supports static route weights, supports BFD check. | ||||
Dynamic Routing: Supports dynamic routing protocols such as RIPv1, RIPv2, OSPFv2 (with BFD detection), and BGP4. | ||||
Strategy Routing: Supports policy-based routing based on incoming interface, source IP, destination IP, etc. | ||||
Link Load Balancing: Provides various load balancing algorithms, supports dual health checks for links, and supports setting priorities and weights for links. | ||||
Supports health check, session persistence, NAT, ALG, VPN, STP, DNS Server, DNS records, DNS transparent proxy, etc. | ||||
High Availability | Supports dual-active hot backup, standby management, VRRP protocol, HA failover conditions and logic, connection session synchronization, setting preemption priority. | |||
Monitoring | Threat visualization, application traffic visualization, user traffic visualization, interface traffic display, system operation information. | |||
Log Report | Storage and export functions for various local logs, supporting log grading; supports remote Syslog logging and supports multiple Syslog servers. | |||
The system provides traffic reports and threat reports, supports email alerts, and allows for the definition of custom email alerts to be triggered under specific conditions. | ||||
Management And Configuration | Supports centralized management, centralized policy analysis, Web management interface, custom packet capture, network debugging. | |||
Backup and recovery of system configuration, administrator login and permission hierarchy; supports SNMP (V1/V2/V3), NTP time synchronization | ||||
SD-WAN, as an emerging networking technology, rapidly establishes SD-WAN networks by deploying u/vCPE devices, virtual gateways, and orchestration controllers, offering flexible and swift network connectivity services to enterprise customers. It has generated significant appeal and practical demand for industries such as retail, catering, education, and healthcare.
SD-WAN technology is currently mainly applied in five business scenarios: government and enterprise branch networking, multi-cloud access, WAN application directional acceleration, retail store access, and emergency activation scenarios. The management platform system needs to support functions such as the activation and operation and maintenance management of multi-tenant services.
Enterprise branch networking scenarios are primarily used for the application of building virtual private networks through SD-WAN technology. Enterprise users can achieve three-layer networking needs between the headquarters and branches, or among branches, both locally and across provinces, and can carry the private network routing of internal users.
With the rapid popularization of the Internet, access resources have greatly enriched, increasing the demand for enterprise branch interconnection, cloud resources, and cloud application access. Connecting through the Internet has become a more economical and flexible approach. At the same time, by utilizing SDN controllers for centralized control, automatic service distribution can be effectively expedited, accelerating the business deployment cycle, increasing the flexibility for enterprise users to order and experience services, and providing users with a rich set of network monitoring and cloud connectivity services.
SD-WAN services can optimize gateway forwarding behavior through application identification and link quality monitoring, achieving optimized and accelerated forwarding performance when multiple nodes are forwarding through the wide area internet.
New retail and the rapid development of supermarkets have a very high demand for the speed of network service activation. It is necessary to quickly, flexibly, and stably establish VPN connections to achieve networking between stores and institutions, and to carry the private network routing for internal users of the enterprise.
With the rapid advancement of urbanization, municipal construction and road renovation projects are carried out annually in different parts of the city. The implementation of these projects poses a significant threat to optical cables, which are at constant risk of being disrupted. Since the 5G network is based on wireless data transmission, utilizing 5G gateways, and through the configuration on both the base station side and the user side, it is possible to achieve wireless 5G line replacement for wired faults that are irreparable or cannot be repaired in the short term.
Product Model | Product Description | Note |
SEG-100A E51C | Interface: 1*USB; 1*WAN port; 4*LAN ports; 1*Combo; IPSEC performance 100M, 16 tunnels | |
SEG-100A W4G | Interface: 1*USB; 1*WAN port; 4*LAN ports; 1*4G; 1*WIFI (optional); 1*Combo; IPSEC performance 100M, 16 tunnels | |
SEG-100A W5G | Interface: 1*USB; 1*WAN port; 4*LAN ports; 1*WIFI (optional); 1*Combo; 1*5G; IPSEC performance 100M, 16 tunnels | |
SEG-100AX2WM | 2-core, interfaces: 2*USB; 4*Ethernet ports; 2*COMBO, memory: 4GB DDR4, storage: EMMC 32G; IPSEC performance 200M, 100 tunnels | |
SEG-100AX4WM | 4-core, interfaces: 2*USB; 4*Ethernet ports; 2*COMBO, memory: 4GB DDR4, storage: EMMC 32G; IPSEC performance 500M, 100 tunnels | |
SEG-100A V16L | 1U, 4-core; 4GB memory; 8GE+4SFP; IPSEC performance 500M, 600 sessions | |
SEG-100A V26L | 1U, 4 cores, 8GB memory, 6GE+2SFP (6 electrical + 2 10G) + 2 expansion slots; IPSEC performance 800M, 3000 tunnels | |
SEG-100A V30L | 2U, 4-core, 8GB memory, 2GB CF card, 64GB/SSD, 6GE+4SFP (6 electrical + 4 optical) + 2 expansion slots; IPSEC performance of 1.5Gbps, 5000 entries | |
SEG-100A V60L | 2U, 4 cores, 16GB memory, 6GE+4SFP (6 electrical + 4 optical) + 6 expansion slots; IPSEC performance 2Gbps, 8000 tunnels | |
SEG-100A V80L | 2U, 16 cores, 32GB memory, 1TB mechanical hard drive, 8 expansion slots; IPSEC performance 5Gbps, 10,000 entries | |
SEG-100A V80H | 2U, 24 cores, 32GB memory, 1TB mechanical hard drive, 8 expansion slots; IPSEC performance 10Gbps, 10,000 entries | |
CL-MD2000-Software | (Controller installation environment): CPU: 8 cores, memory: 32GB, hard disk: 500GB or more, operating system: Windows Server 2012, Windows Server 2012 R2 or above |
SD-WAN, as an emerging networking technology, rapidly establishes SD-WAN networks by deploying u/vCPE devices, virtual gateways, and orchestration controllers, offering flexible and swift network connectivity services to enterprise customers. It has generated significant appeal and practical demand for industries such as retail, catering, education, and healthcare.
SD-WAN technology is currently mainly applied in five business scenarios: government and enterprise branch networking, multi-cloud access, WAN application directional acceleration, retail store access, and emergency activation scenarios. The management platform system needs to support functions such as the activation and operation and maintenance management of multi-tenant services.
Enterprise branch networking scenarios are primarily used for the application of building virtual private networks through SD-WAN technology. Enterprise users can achieve three-layer networking needs between the headquarters and branches, or among branches, both locally and across provinces, and can carry the private network routing of internal users.
With the rapid popularization of the Internet, access resources have greatly enriched, increasing the demand for enterprise branch interconnection, cloud resources, and cloud application access. Connecting through the Internet has become a more economical and flexible approach. At the same time, by utilizing SDN controllers for centralized control, automatic service distribution can be effectively expedited, accelerating the business deployment cycle, increasing the flexibility for enterprise users to order and experience services, and providing users with a rich set of network monitoring and cloud connectivity services.
SD-WAN services can optimize gateway forwarding behavior through application identification and link quality monitoring, achieving optimized and accelerated forwarding performance when multiple nodes are forwarding through the wide area internet.
New retail and the rapid development of supermarkets have a very high demand for the speed of network service activation. It is necessary to quickly, flexibly, and stably establish VPN connections to achieve networking between stores and institutions, and to carry the private network routing for internal users of the enterprise.
With the rapid advancement of urbanization, municipal construction and road renovation projects are carried out annually in different parts of the city. The implementation of these projects poses a significant threat to optical cables, which are at constant risk of being disrupted. Since the 5G network is based on wireless data transmission, utilizing 5G gateways, and through the configuration on both the base station side and the user side, it is possible to achieve wireless 5G line replacement for wired faults that are irreparable or cannot be repaired in the short term.

Product Model | Product Description | Note |
SEG-100A E51C | Interface: 1*USB; 1*WAN port; 4*LAN ports; 1*Combo; IPSEC performance 100M, 16 tunnels | |
SEG-100A W4G | Interface: 1*USB; 1*WAN port; 4*LAN ports; 1*4G; 1*WIFI (optional); 1*Combo; IPSEC performance 100M, 16 tunnels | |
SEG-100A W5G | Interface: 1*USB; 1*WAN port; 4*LAN ports; 1*WIFI (optional); 1*Combo; 1*5G; IPSEC performance 100M, 16 tunnels | |
SEG-100AX2WM | 2-core, interfaces: 2*USB; 4*Ethernet ports; 2*COMBO, memory: 4GB DDR4, storage: EMMC 32G; IPSEC performance 200M, 100 tunnels | |
SEG-100AX4WM | 4-core, interfaces: 2*USB; 4*Ethernet ports; 2*COMBO, memory: 4GB DDR4, storage: EMMC 32G; IPSEC performance 500M, 100 tunnels | |
SEG-100A V16L | 1U, 4-core; 4GB memory; 8GE+4SFP; IPSEC performance 500M, 600 sessions | |
SEG-100A V26L | 1U, 4 cores, 8GB memory, 6GE+2SFP (6 electrical + 2 10G) + 2 expansion slots; IPSEC performance 800M, 3000 tunnels | |
SEG-100A V30L | 2U, 4-core, 8GB memory, 2GB CF card, 64GB/SSD, 6GE+4SFP (6 electrical + 4 optical) + 2 expansion slots; IPSEC performance of 1.5Gbps, 5000 entries | |
SEG-100A V60L | 2U, 4 cores, 16GB memory, 6GE+4SFP (6 electrical + 4 optical) + 6 expansion slots; IPSEC performance 2Gbps, 8000 tunnels | |
SEG-100A V80L | 2U, 16 cores, 32GB memory, 1TB mechanical hard drive, 8 expansion slots; IPSEC performance 5Gbps, 10,000 entries | |
SEG-100A V80H | 2U, 24 cores, 32GB memory, 1TB mechanical hard drive, 8 expansion slots; IPSEC performance 10Gbps, 10,000 entries | |
CL-MD2000-Software | (Controller installation environment): CPU: 8 cores, memory: 32GB, hard disk: 500GB or more, operating system: Windows Server 2012, Windows Server 2012 R2 or above |